Single Sign-On (SSO) setup in 6clicks
6clicks SSO is designed to work with a few select Identity Providers (IdP). This article provides guidance for the overall setup with links to specific instructions for Microsoft Entra ID, Okta, and PingID.
Single Sign-On (SSO) setup in 6clicks requires the following steps:
This should, as much as possible, be completed in one session to avoid errors.
Each identity provider handles SSO via OIDC a little differently. The setup instructions provided above are only one way to set up SSO at each IdP. However, depending on how your organization is architected, there are alternate ways.
Sign in to 6clicks with a user account that has permission to administer Single Sign-On.
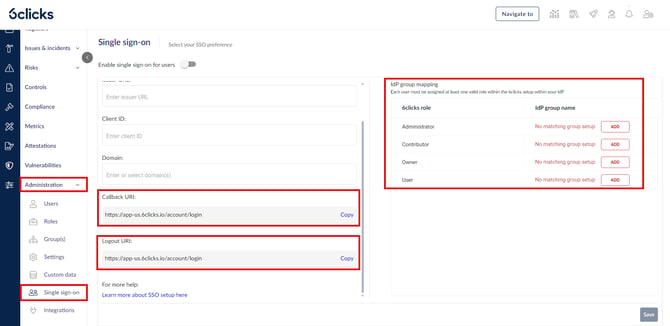
Navigate to Administration → Single Sign-On. Note the Information within the Callback URIs, Logout URI, and Roles fields which is necessary for setting up the 6clicks application in your identity provider.
For the Roles, note or create the 6clicks roles you will be using in your single sign-on environment. You will create corresponding groups in your identify provider to map to these roles. If the groups in the identify provider are created in the format "6clicks-role-<role name>" e.g., 6clicks-role-administrator, no additional mapping should be required. Learn more about user roles and permissions at 6clicks.
Configure identity provider settings
Create an OIDC (OpenID Connect) application with the 6clicks settings for your tenant. Follow the instructions provided for your particular identity provider:
Finish the SSO setup in 6clicks
Once the identify provider has been configured, return to the 6clicks SSO page to complete the configuration.
1. Enable Single Sign-On for users
2. Select the external identity provider
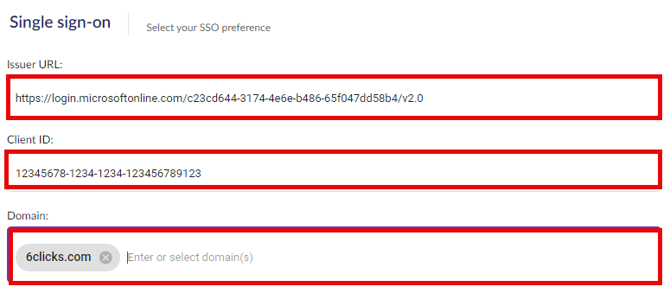
3. Add in the Issuer URL, Client ID, and Domain values from that provider. See the configuration instructions for the respective identity providers
-
Issuer URL
-
Client ID: May be identified as the application (client) ID
-
Domain: Enter the domain used by your organization. Any user with an email address with this domain will be required to use SSO to access the 6clicks application.
If your organization operates multiple domains, enter each domain into the Domain field and press 'Enter' on your keyboard to add them individually.
For example, with Azure AD/Entra ID:
Find more information on configuring the supported Single Sign-On identity provider settings here.
Learn more about user management here.
Learn more about Single-Sign On user scenarios here.