This article introduces just-in-time provisioning, easier login options, and added security measures for Single-Sign-On integrations to streamline user management and improve access to 6clicks team accounts.
PLEASE NOTE: This article only applies to existing 6clicks SSO integrations prior to April 15th, 2023.
The content below highlights potential issues faced by existing SSO users during migration.
Potential login issues
- Domains of users that have been using/connected to SSO in the past will now be automatically listed to enforce SSO, leading all the users within that domain to only being able to login with SSO
- In addition to above, all the users who are now enforced to login using SSO, must be assigned to the respective application on their IdP in order to be able to login
What needs to be done to avoid this?
- For the tenant, make a list of the domains that have been connected to SSO in the past
- On your IdP, assign all the users to the 6clicks application
- Inform the users of the new changes
Who is responsible for making these updates? And where can the changes be made?
- A 6clicks admin can see all individual user IdP status in 6clicks from Administration > Users > Oka/Azure status.
- All user details can also be downloaded from Administration > Users > More > Export to excel
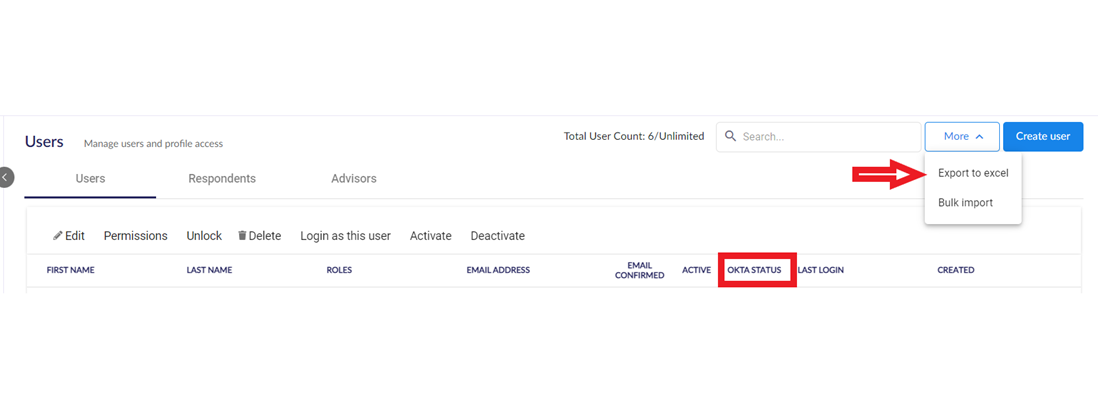
- All user details can also be downloaded from Administration > Users > More > Export to excel
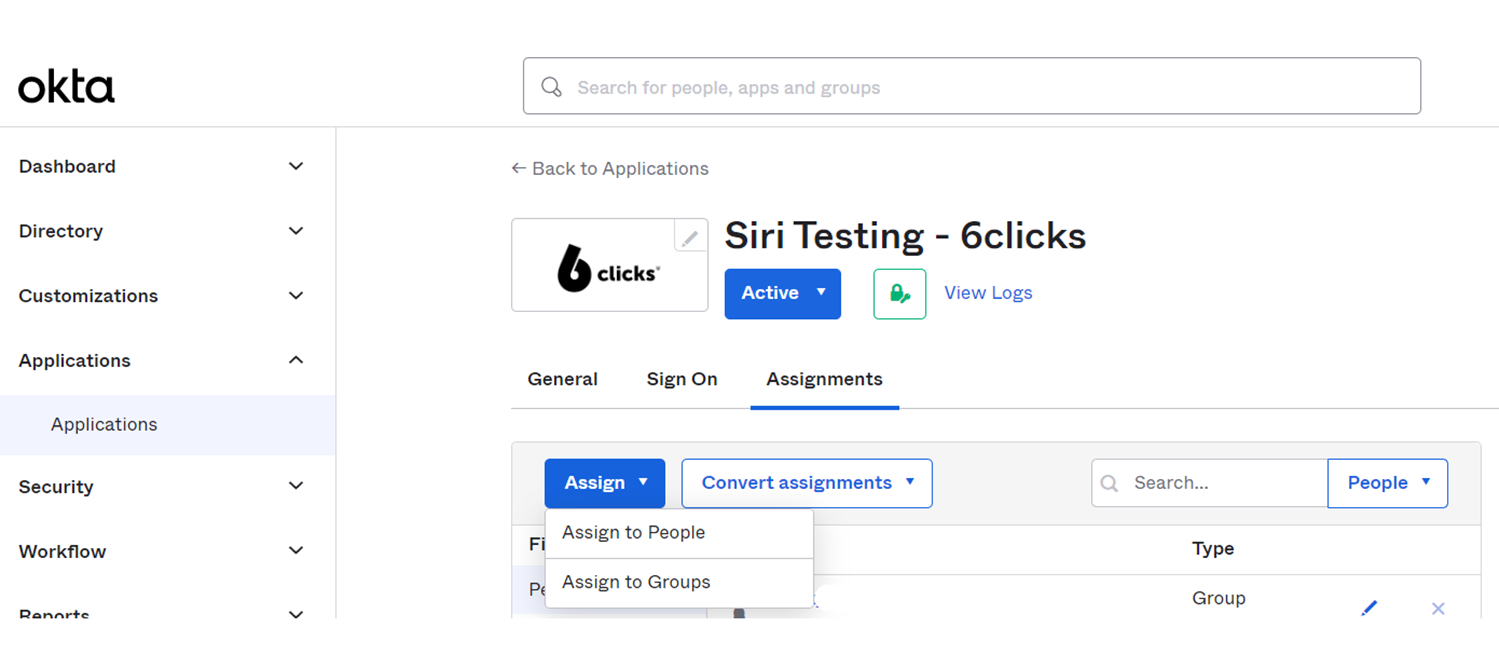
- IdP Admin is responsible for assigning users to the 6clicks application in their IdP. Below are references on how to assign;
- Okta
- Azure
- Okta
- If a user is not able to login (when SSO is enabled), then they must reach out to the company admin instead of 6clicks-support
Potential role change issue (Priority – Medium)
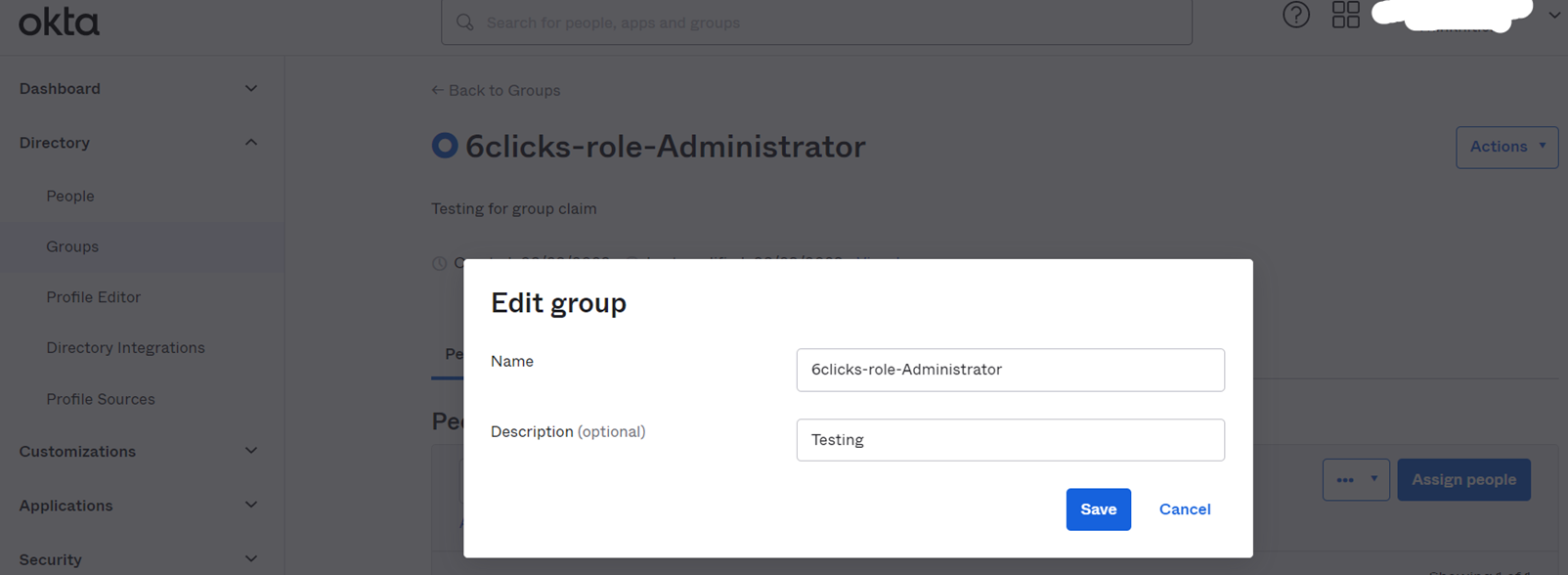
6clicks is now able to automatically update roles to match with group claim name on IdP, if the group claim is in supported format 6clicks-role-<role-name> (for example; 6clicks-role-administrator).
The role on 6clicks will only be updated if the role name provided in the above-mentioned group claim matches to any role on 6clicks
- If the group name on IdP does not match with roles in 6clicks;
- When a new user is created through IdP > user is assigned a default role on 6clicks
- When an existing user logs in through IdP > no changes made to their role on 6clicks
- If the group name on IdP matches with role(s) in 6clicks;
- When a new user is created through IdP > user is assigned the respective role
- When an existing user logs in through IdP > matching role is updated for the user
When will this change happen?
If the group name follows the above-mentioned format, the role changes will happen in 6clicks during SSO authentication of the user.
What if my IdP group name doesn’t follow 6clicks supported format?
If the group names on the company’s IdP do not follow the above-mentioned format, there won’t be any automatic changes to the user roles and will remain as it is in 6clicks.
Who is responsible to look into this?
Respective IdP admin with access to editing/creating groups can check and verify the group names, and take the below actions;
- If no changes to roles are required initially, the group name on IdP does not have to follow the format 6clicks-role-<role-name>.
- If it does, make sure users are assigned to respective groups as per roles in 6clicks
- If any changes to roles are required, the group name on IdP should be updated to follow the format 6clicks-role-<role-name> and make sure the same role exists on 6clicks
- Assign users to respective groups as required on IdP
- Azure – create groups using the above-mentioned format
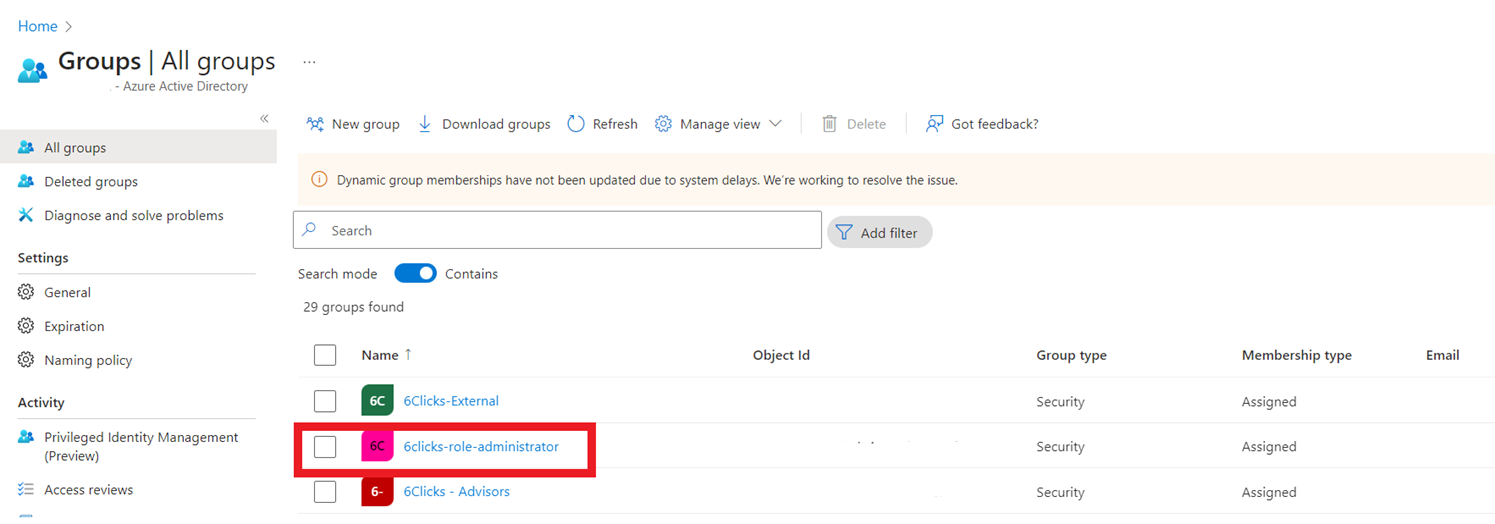
- Okta – Create/edit group name in above mentioned format
- If roles are updated automatically, and users lose any required role-based access such as ‘Administrator’ in 6clicks;
- they can contact the respective IdP admin to update their role on IdP and inform them of the issue
Update IdP settings to login from IdP dashboard to 6clicks
With the new updates, users can now login to 6clicks through their IdP dashboard. In order to do so, the respective IdP admin must enable the application on the user's IdP dashboard (where required).
Note: For any issues interfacing with 6clicks, submit a ticket via Submit Support Ticket - otherwise provide these instructions to your idP (Identity Provider).